Security at its Highest Peak
Real-time vulnerabilities, scalable security, and certified hackers at your fingertips. A streamlined PTaaS platform to keep your business secure and one step ahead of threats.
Start Your First Pentest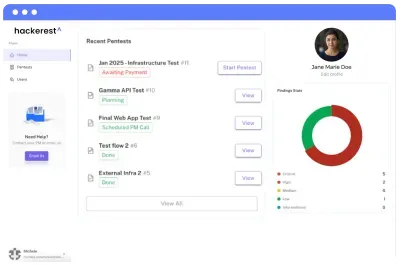
Why choose Hackerest
Launch a Pentest in Days, Not Weeks
No more long waits. Start a pentest within days and get immediate access to our network of 5+ certified hackers, ensuring rapid security coverage for your business.
Reduce Security Risk
Catch vulnerabilities early before they become breaches. With Hackerest’s streamlined PTaaS platform, you get actionable findings 2x faster than traditional pentesting.
Accelerate Remediation
Stay agile and address vulnerabilities quickly. Hackerest helps you remediate 50% faster by providing continuous insights and easy-to-understand reports
Access Elite Hackers On-Demand
Tap into a global network of highly certified, expert hackers when you need them. Our crowdsourced model ensures you’re always covered, eliminating the need to wait for scarce security resources.
Continuous Testing, Not Just Snapshots
Traditional pentests are periodic and static. Hackerest offers ongoing, dynamic testing so your security posture evolves alongside your applications and infrastructure.
Real-Time Visibility
Monitor findings as they are discovered through our intuitive platform. Stay informed, prioritize risks, and act faster to protect your assets.

Our Clients
These companies opened their doors to our hackers - and got real insights into their security posture.
Elevating Security All in One Platform
Unified Dashboard
View all your security testing efforts in one place. Visualize your risk posture, see upcoming tests, and track findings by severity and status for a clear, high-level perspective.
Schedule and Launch Tests Easily
Streamline the process of launching a pentest. Choose your start date, define your scope, and get testing underway within days, not weeks.
Dedicated Project Manager
A dedicated project manager oversees the entire testing process, collaborating with you to define objectives, ensure requirements are met, and guide your project to successful completion.
Flexible and Scalable
Whether you’re a startup or an enterprise, our platform adapts to your needs. Get tailored solutions that match your security maturity without overextending your resources.
Real-Time Collaboration
Collaborate directly with our expert hackers. Understand findings, discuss impacts, and implement remediation strategies faster with seamless communication.
Track Real-Time Results
Effortlessly track the status of your security tests and view results in real-time. Stay informed every step of the way with live updates and detailed insights.
Contextual Insights and Expert Advice
Receive data-driven insights into vulnerabilities and their criticality. Our experts provide evidence-based Proof of Concepts (PoC) to help determine the most effective mitigation strategies.
How it Works
Launching a Pentest with Hackerest is Easy!
Book a Demo
Get a personalized walkthrough of our platform and see how Hackerest can secure your business.
Access Your Account
Sign in to your secure dashboard and explore our intuitive PTaaS platform.
Schedule a Pentest
Choose your start date and define your scope. Flexibility to launch when you need it most.
Monitor in Real-Time
Watch the pentest progress live, track findings as they’re discovered, and stay informed every step of the way.
Download Your Report
Receive a detailed, actionable report with prioritized vulnerabilities and remediation steps.

Our Certifications
At Hackerest, we believe that top-tier security requires top-tier talent. Our expert hackers hold industry-leading certifications that demonstrate deep knowledge and proven skills in offensive security.
Our Services
At Hackerest, we offer specialized penetration testing services tailored to different aspects of your digital infrastructure. Our comprehensive approach ensures that vulnerabilities are identified and remediated efficiently, helping you maintain a strong security posture.
Web Application Penetration Test
Our web application pentests combine automated scans with meticulous manual testing to uncover vulnerabilities that automated tools might miss. We provide:
Thorough Analysis of authentication, authorization, input validation, and data handling.
Detailed Reports with prioritized findings and step-by-step remediation guidance.
Proof of Concepts (PoCs) to illustrate how vulnerabilities can be exploited and their potential impact.
Continuous Support to ensure fixes are effective and security improvements are implemented smoothly.

Network Penetration Test
Our network pentests evaluate your internal and external networks to identify weaknesses and potential attack vectors. We offer:
Comprehensive Scanning and Manual Testing to detect misconfigurations, outdated systems, and insecure services.
Simulated Attacks to demonstrate how an attacker could exploit network vulnerabilities.
Clear, Actionable Recommendations to strengthen your network defenses.
Guided Remediation to ensure your infrastructure is hardened against future threats.
Cloud Penetration Test
We specialize in securing cloud environments, including AWS, Azure, and GCP. Our cloud pentests focus on:
Configuration Reviews to ensure cloud resources (e.g., storage, databases, compute instances) are set up securely.
API Security Testing to identify weaknesses in cloud-based APIs and prevent exploitation.
Identity and Access Management (IAM) Audits to enforce least-privilege access and avoid privilege escalation.

Are you a Hacker? Join Hackerest.
At Hackerest, our pentesters are elite security professionals driven by a passion for uncovering vulnerabilities and making the digital world safer. They thrive on challenging tests, real-world impact, and continuous growth. If you love tackling complex security challenges and collaborating with forward-thinking teams, Hackerest is your community.
We’re more than just a platform – we’re a network of innovators dedicated to precision, quality, and growth. Join us and help redefine the future of cybersecurity.
How to join Hackerest?
Application
Submit your application and provide details about your skills, experience, and passion for cybersecurity. Highlight your achievements and showcase what makes you stand out.
Assessment
Prove your expertise through a challenging Capture The Flag (CTF) exercise. Designed to test your problem-solving skills and technical acumen, the CTF replicates real-world scenarios to ensure you’re ready for the complexities of professional pentesting.
Interview
Participate in a one-on-one interview with our team. This step allows us to get to know you better, discuss your goals, and ensure we’re the right fit for each other.
Sign Terms of Engagement
Review and agree to our collaboration terms. Once finalized, you’ll officially become part of the Hackerest community, ready to take on exciting pentesting projects.
Continuous Evaluation
Your performance will be continuously evaluated based on the quality and impact of your work. High standards are rewarded with more opportunities, ensuring a mutually beneficial collaboration


Revolutionizing Pentesting for a Safer Digital World
At Hackerest, we envision a world where security is proactive, continuous, and accessible. With over a decade of experience in cybersecurity, we understand the challenges businesses face in securing their digital assets. We created Hackerest to empower organizations with cutting-edge Pentest as a Service (PTaaS), combining real-time insights, certified hackers, and an intuitive platform. Our mission is to make security a seamless part of your growth, enabling you to innovate with confidence and stay ahead of threats.
Frequently Asked Questions
Our pentesters are part of an elite, highly selective pool of security professionals. We conduct comprehensive screening to verify their qualifications, technical expertise, and proven track record of success in identifying and addressing vulnerabilities.
Every candidate goes through an in-depth vetting process, including technical assessments, practical evaluations, and a review of their previous achievements. Only those who meet our stringent requirements join the Hackerest community.
Multiple pentesters are assigned to each assessment, ensuring continuous peer review throughout the process. This collaborative approach guarantees accurate findings and minimizes the risk of oversight.
Customers receive regular updates on the progress of their pentests, along with access to an internal chat feature for direct communication with the pentesters conducting the assessment. This fosters transparency and allows customers to ask questions, provide additional context, or clarify requirements to ensure comprehensive coverage.
Hackerest implements an ongoing performance review system to monitor and maintain the quality of work delivered by our pentesters. This includes customer feedback and internal evaluations after each engagement, ensuring that only the best professionals continue to represent Hackerest.
We encourage customers to interact with the pentesters directly during the process, enabling real-time adjustments and deeper insights into findings. This collaboration ensures that the tests align with your unique security needs and maintain a high-security bar.
Have any other question? What are you waiting, feel free to reach out! Someone from the support team will help you right away


Looking for more information?
Get in touch with us for custom pricing tailored to your specific needs. We'll provide a transparent quote with no hidden fees.



















